2024 HIPAA Trends and Statistics
Read this blog to learn how 2024 compared to 2023 regarding HIPAA Security, Breach Notification, and Privacy Rules trends.

Read this blog to learn how 2024 compared to 2023 regarding HIPAA Security, Breach Notification, and Privacy Rules trends.

Every year, SecurityMetrics conducts surveys of over 100 healthcare providers and professionals who are responsible for becoming HIPAA compliant. These professionals typically have less than 500 employees but work closely with much larger organizations, sharing patient data. These statistics are important because they reflect the current data security trends among all healthcare organizations, regardless of size.
Read this blog to learn how 2024 compared to 2023 regarding HIPAA Security, Breach Notification, and Privacy Rules trends.
Of the 100 healthcare entities responding, 71% of them reported that they encrypt patient data, per HIPAA regulations. 81% responded that they destroy or delete sensitive data, which is less than the previous year. 69% of organizations say that they use MFA (multi-factor authentication), and 72% have automatic timeouts/logouts enabled on all of their workstations.
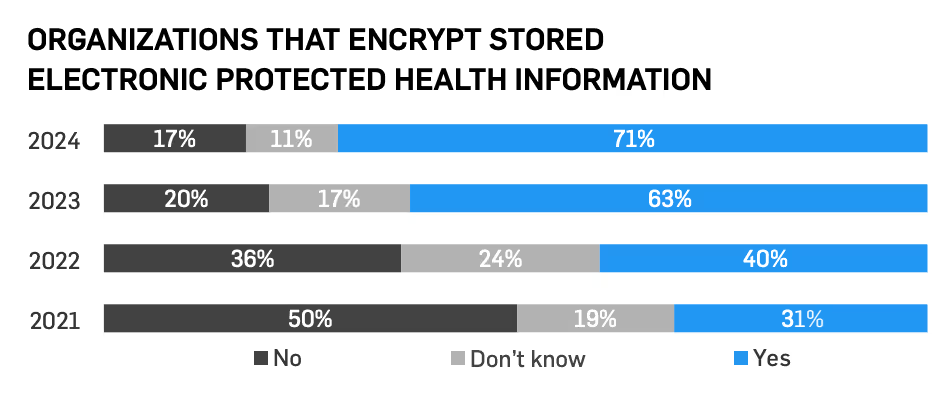
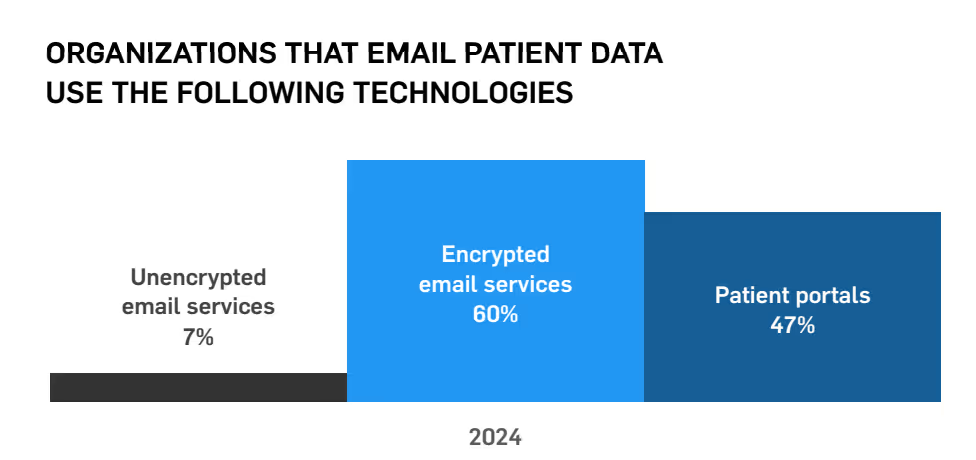
55% of organizations reported that they don’t send emails containing patient data, which is lower than 2023. However, 60% report emailing patient data through encrypted email services, which is an improvement. 47% of professionals said that they use a patient portal to communicate patient data, and only 7% report sending patient data through unencrypted emails.
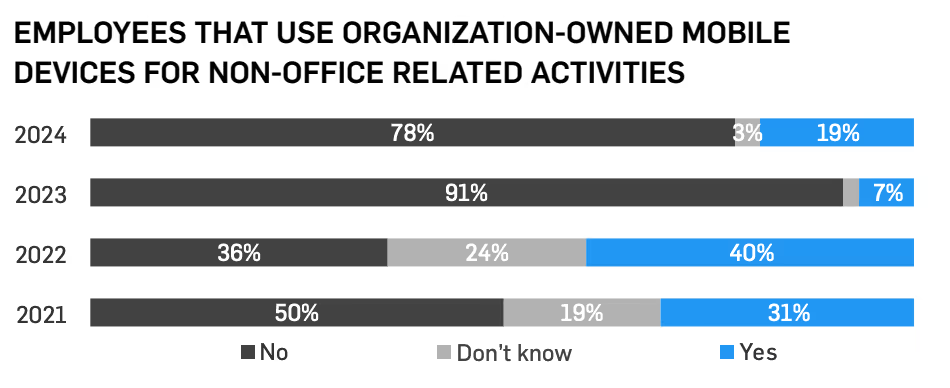
78% of healthcare providers report that they don’t let employees use organizationally owned mobile devices for personal use. 43% have a mobile device policy in place, per HIPAA rules, including a BYOD (bring your own device policy). Unfortunately, 40% report that they don’t use mobile encryption, which is higher than 2023.
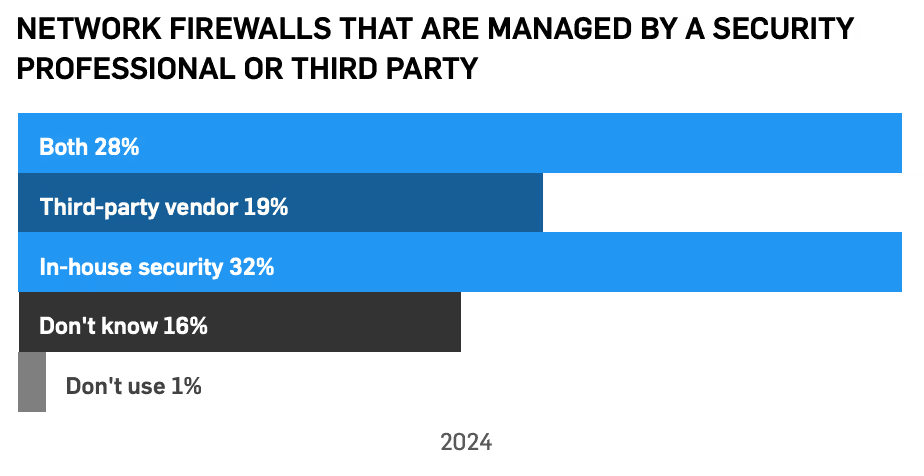
Staff education efforts have paid off, as only 16% of employees report not knowing what firewall their organization uses, which is an improvement from last year. Interestingly, 51% of respondents use a security professional or third party provider to manage their network firewall. Roughly 21% review their firewall rules at least quarterly, which is also an improvement from last year.
58% of respondents said that they store system logs per HIPAA requirements, but only 23% review their data prevention tool logs at least monthly. When it comes to reviewing access controls, 57% review at least annually.
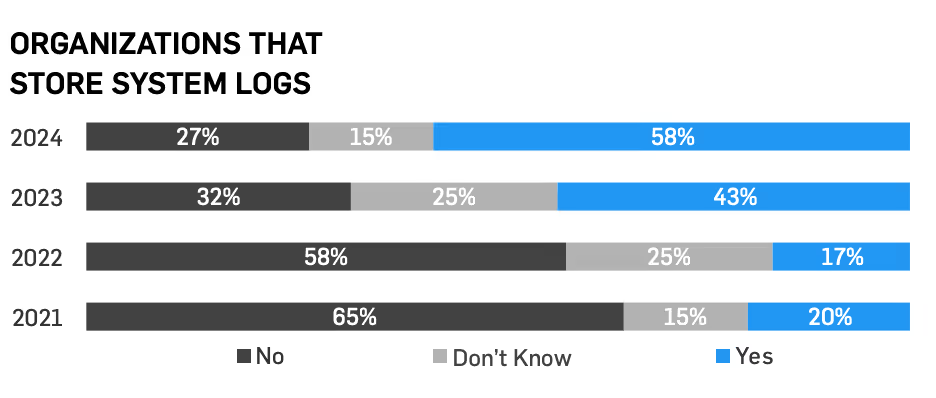
55% report conducting vulnerability scans and 26% conduct scans at least quarterly, which are both higher than 2023’s report.
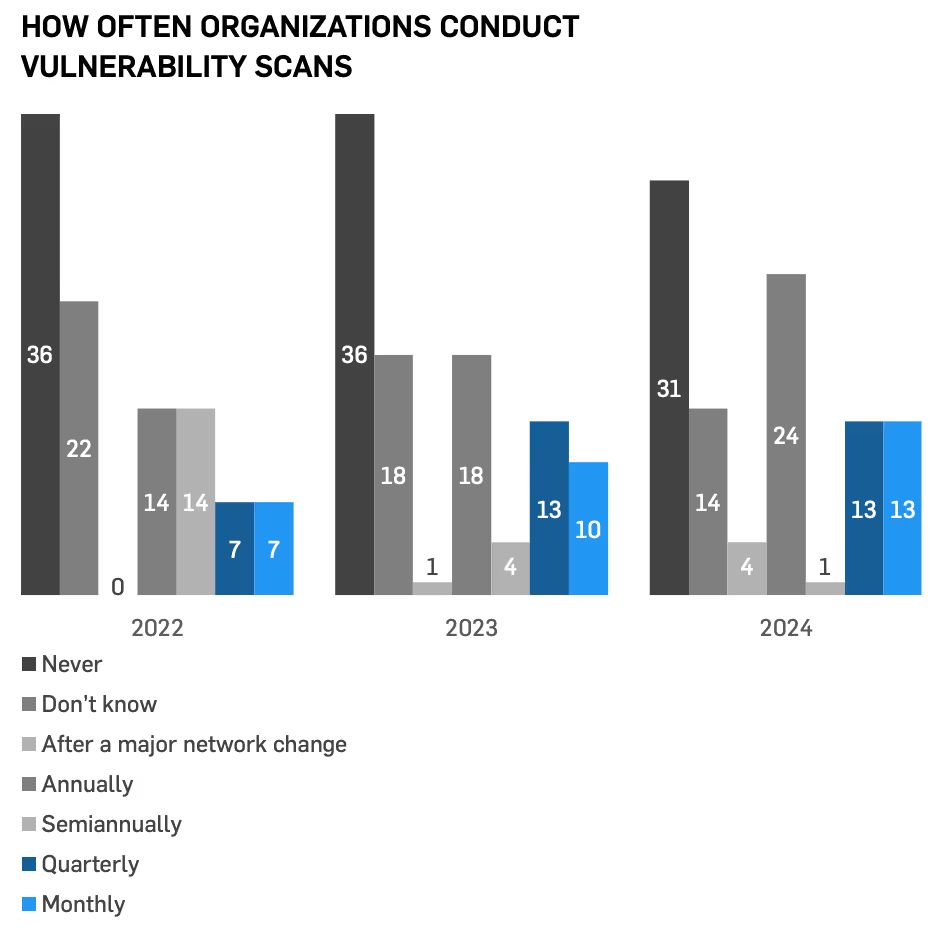
Coming in as the same as last year, 22% report conducting penetration tests, with 31% performing their pen tests yearly.
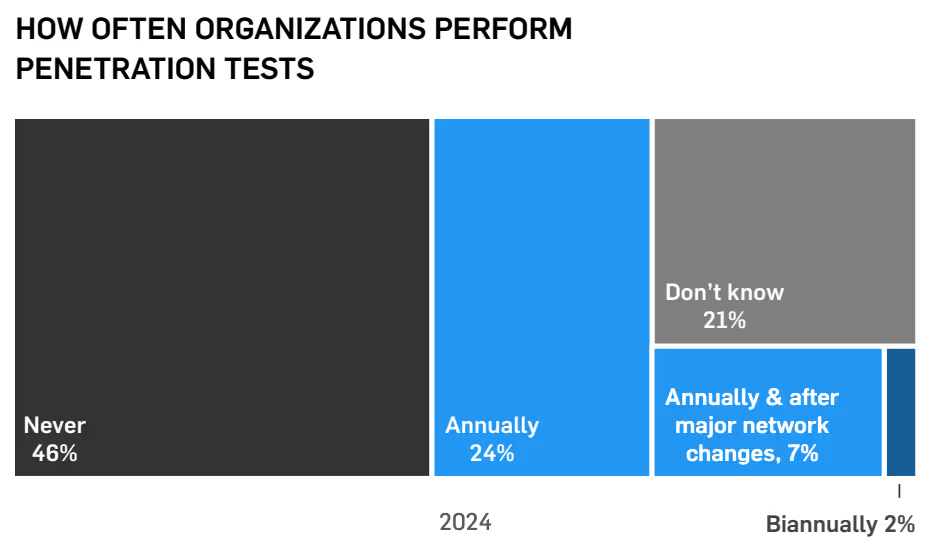
41% of respondents report reviewing their BAA (business associate agreement) documentation at least annually, with 48% updating their NPP (notice of privacy practices) at least annually. When it comes to reviewing HIPAA compliance documentation, 72% review at least annually.
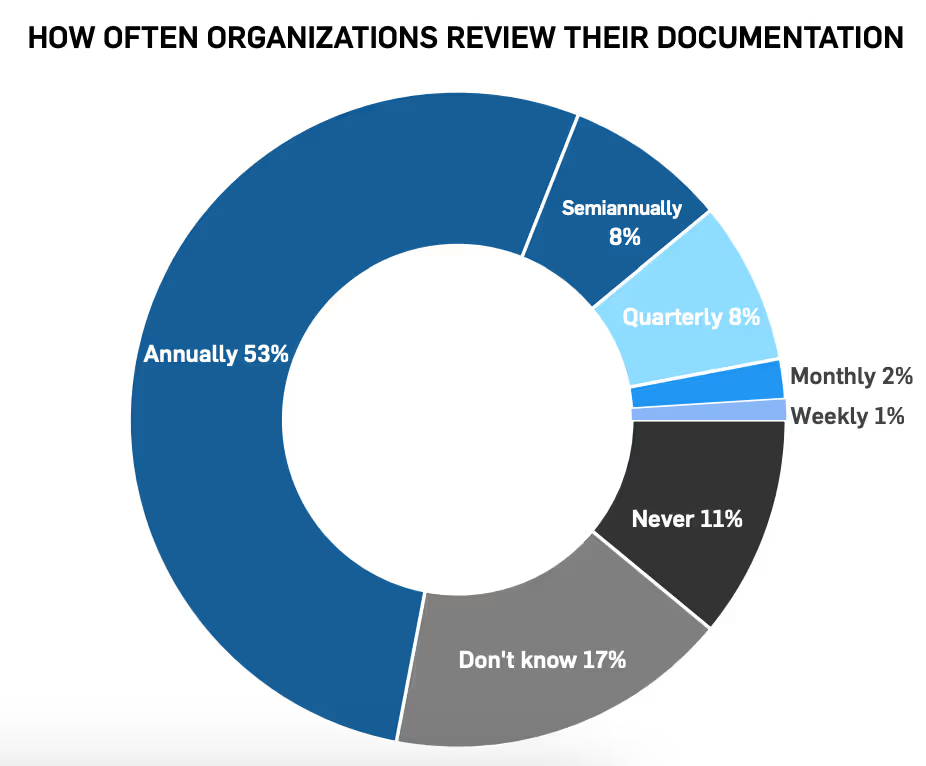
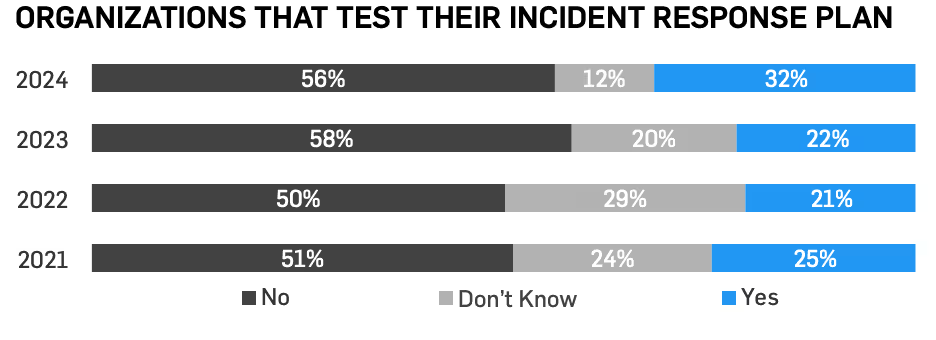
Unfortunately, 7% of respondents don’t have any response plan policies in place, including an incident response plan, disaster recovery plan, or business continuity plan. Fortunately, this percentage is lower than then the previous year, demonstrating more businesses are taking response plans seriously. 71% review their response plan at least annually and 32% report testing their incident response plan.
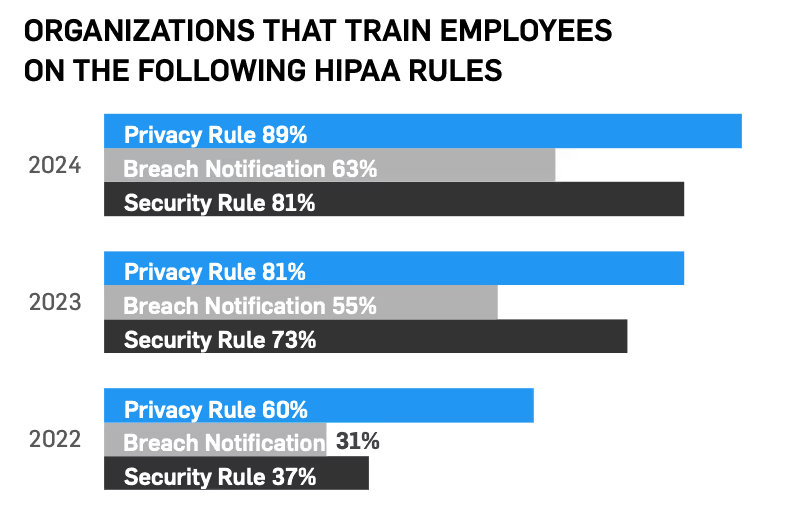
Perhaps one of the most important trends to analyze is how frequently employees are being trained on HIPAA compliance. This year, 62% report training employees annually with 81% providing HIPAA Security Rule training, 63% training on HIPAA Breach Notification Rule, and 89% providing HIPAA Privacy Rule Training. Only 36% of respondents say they don’t test employees on their HIPAA training, and 50% test employees on HIPAA training at least annually, an improvement from last year.
Adequately training your staff on HIPAA policies and rules is as vital as ever, with an increase in attack trends, particularly sophisticated attacks on the healthcare industry. This means your staff needs regular social engineering and phishing training, so they can identify potential scams ahead of time.
Above all, remember to practice good “cyber hygiene” so attackers have limited access to your network and employees.