With over 20 years in the industry, we have found that these HIPAA compliance best practices are most helpful in securing your organization.

If documentation is done correctly, it can create a baseline security standard for every process, workforce member, and system at your organization.
Without a recorded comparison of last year’s security plan, your future efforts become much more difficult.
Here are three reasons to keep proper documentation:
Remember to make sure you’re actually implementing the policies you document. If you haven’t implemented anything in your documentation, this is a major detriment to you, your PHI, and your organization.
A large part of your HIPAA compliance process and effort should be spent on documentation.
Many organizations are confused about what exactly they should document and how they should document it. Generally speaking, you should record the who, what, when, where, how, and why of everything related to PHI in your environment. Documentation should demonstrate in writing where you are today, where you’ve progressed over the years, and what your plan is for the future.
Your documentation should answer questions like:
To answer these broad questions, dive into the detailed answers of more specific and technical questions, such as:
The biggest disservice you could do while meeting HIPAA documentation requirements is to spend weeks gathering paperwork, and then place it on a shelf until next year. HIPAA documentation is only as useful as it is accurate.
Just like all of your other weekly activities, documentation should be an ongoing part of your entire business-as-usual security strategy.
Try to examine and adjust at least one piece of documentation each week or as you make organizational updates. Don’t pile it into one day or one month at the end of the year.
Workforce members are often considered the weakest link in PHI security and HIPAA compliance by most security professionals. If you don’t give your workforce specific rules and training, they won’t be able to keep up with constantly changing security best practices and secure PHI. Plus, if employees are trained only once, they might forget policies and procedures.
Consistent workforce training and education will remind them that both privacy and security are important, and it will show them how to create good security habits.
You should train your staff regularly (e.g., monthly). Training doesn’t have to be lengthy and detailed. You can break up training into monthly small and simple trainings (e.g., 20 minute presentations), making it easier to remember and implement procedures. For example, consider having specific training about the following topics:
Social media use has become even more prevalent. If employees irresponsibly use social media, their actions can easily lead to serious HIPAA violations. Make sure staff understand the consequences of not following your HIPAA policies.
As you set up your training plan, consider the following tips:
In addition to your training plan, make sure you have and follow appropriate sanctions for workforce members that do not comply with your policies and procedures.
Third party HIPAA assessors are not your enemy; they want to help you make your organization more secure for your workforce members and your patients. But if you aren’t prepared, a government-mandated audit can become a major challenge.
A HIPAA audit isn’t necessarily the result of a whistleblower or a possible HIPAA violation. It’s mainly for the Office of Civil Rights(OCR) to assess and gain an understanding of how healthcare providers are doing with HIPAA compliance, and to see if any changes need to be made.
There are a few reasons why your organization may be audited:
All covered entities and their business associates are eligible for a HIPAA audit.
Conducting audits within your organization can help you find resolvable problems in your security. It’s best to do internal audits periodically to find new issues that may appear.
Organizations should engage a third-party security expert to help with conducting a proper security assessment. A security assessor will have experience in HIPAA (and many other security mandates)and will be able to see your organization from an external view(which is what malicious attackers are doing).
If you have time, conducting an internal audit is a good idea to find and resolve any problems before your third-party onsite audit.
The amount required to budget for HIPAA compliance depends on your organization. Here are a few variables that will factor into the cost of your overall compliance:
Having the proper security budget protects not just your organization but your patients as well.
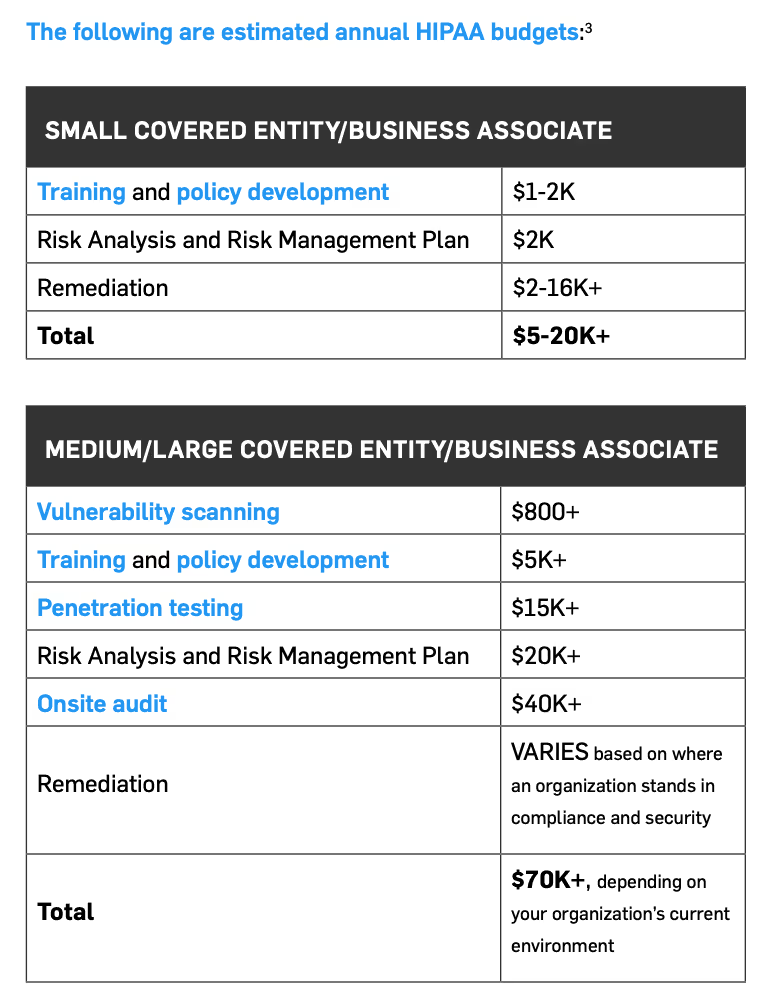
Keep in mind, this is far cheaper than paying for a data breach, which can amount to $180,000 to $8.3 million and above.
With over 20 years in the industry, we have found that these HIPAA compliance best practices are most helpful in securing your organization. For more detailed information on any of these topics, download our free HIPAA Guide.