How to Maintain HIPAA Compliant Firewalls
Simply installing a firewall on your organization’s network perimeter doesn’t secure your network or make you HIPAA compliant. Proper configuration is critical for HIPAA compliant firewalls.

Simply installing a firewall on your organization’s network perimeter doesn’t secure your network or make you HIPAA compliant. Proper configuration is critical for HIPAA compliant firewalls.

Network firewalls are vital for your HIPAA compliance efforts. A firewall’s purpose is to filter potentially harmful Internet and other untrusted network traffic to protect valuable PHI and other sensitive resources.
Simply installing a firewall on your organization’s network perimeter doesn’t secure your network or make you HIPAA compliant. Proper configuration is critical for a firewall to be effective. Proper installation, configuration and management of HIPAA compliant firewalls can be a difficult task and an added burden to IT teams.
Many organizations opt to have a third party manage their firewalls. While this isn’t required by HIPAA, having a managed firewall can help you with complex firewall rules and management so that your firewalls remain secure and helps ensure your firewall is working properly.
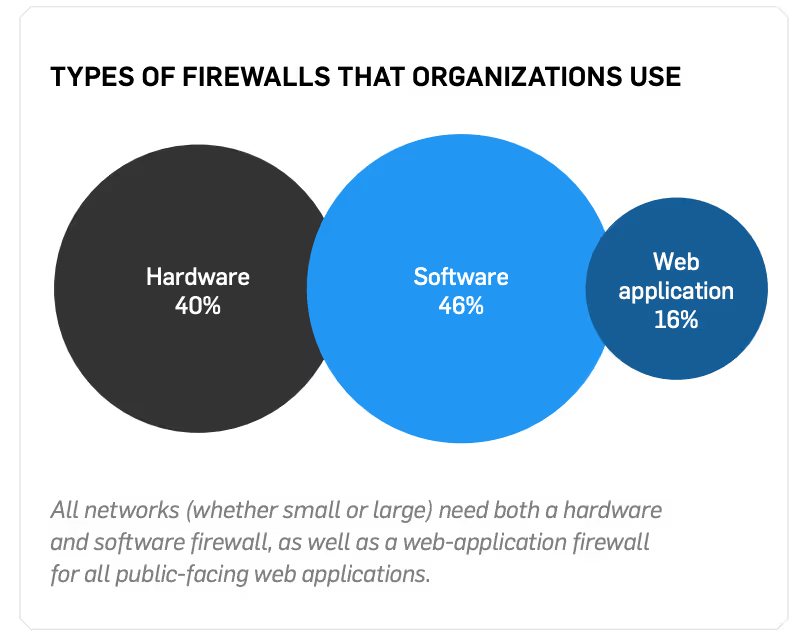
Network firewalls can be software or hardware technologies that provide a first line of defense to a network. Firewalls restrict incoming and outgoing network traffic through rules and criteria configured by the organization. Secure networks rely on hardware, software, and web application firewalls.
Firewalls can be used to implement segmentation (in other words, separation) within an organization’s network. By creating separate networks dedicated to PHI access (e.g., EHR/EMR systems) firewalled off from the rest of the day-to-day traffic, it is possible to ensure that patient data is only sent to known and trusted sources.
Healthcare organizations often make the mistake of setting up a flat network where everything inside the network can connect to everything else. They may have one firewall at the edge of their network, but nothing to manage the traffic inside their network. This is risky because unrestricted access between systems increases the risk of a HIPAA violation or data breach. All networks need both a hardware and a software firewall.
See also: White Paper: How to Implement and Maintain PCI Compliant Firewalls
A hardware firewall, or a perimeter firewall, is typically installed at the outside edge of an organization’s network to protect internal systems from malware and other threats on the Internet. Perimeter firewalls are used to manage all traffic to or from the internet and other outside networks. Any publicly-accessible services such as email, VPN, and web servers are generally maintained in a demilitarized zone (DMZ) network.
A perimeter firewall should be configured to restrict all traffic traversing the perimeter of the network, including DMZ traffic, so that only necessary ports and connection types are permitted.
Software firewalls, or Internal network firewalls, are also normally used inside the environment to create isolated network segments and to separate networks that have access to PHI from networks that don’t. Any internal network that handles sensitive data should be protected by an internal firewall from other internal networks that contain devices with lower security requirements.
All unnecessary traffic to and from sensitive networks should be denied such that only legitimate, justified traffic is permitted. For example, a guest WiFi network should not have access to any network used to handle PHI.
External and internal firewall functions may be consolidated into a firewall device in smaller networks.
A web application firewall (WAF) should be implemented in front of public-facing web applications to monitor, detect, and prevent web-based attacks. WAFs are different from network firewalls because they work at the application layer rather than the network layer and they specialize in one specific area: monitoring and blocking web-based traffic.
A WAF can protect web applications that are visible or accessible from the Internet. To do this, your WAF must be up-to-date, generate audit logs, and either block cyberattacks or generate a cybersecurity alert if it suspects an imminent attack.
A personal firewall, also called a host-based firewall, is a software firewall installed directly on a computer. It manages traffic to and from the individual computer. Many server and workstation operating systems include personal firewalls. Alternatively, antivirus solutions or other applications may also perform this function. A personal firewall can protect a device from many outside threats, including many threats from other devices that share the same network. It should be enabled and configured for any laptop computers that commonly connect to sensitive data networks.
SEE ALSO: Firewalls 101: 5 Things You Should Know
A common firewall mistake is assuming that they are a ‘plug and play’ technology. Organizations often don’t realize it’s necessary to configure the firewall to help with their unique environment.
To properly configure HIPAA compliant firewalls you need to restrict and control the flow of traffic as much as possible, specifically around networks with PHI access.
Depending on how complex your environment is, you might require many firewalls to ensure all systems are separated correctly. The more controls you have, the less chance an attacker has at getting through unprotected Internet connections.
Remember, your firewall is your first line of defense, so you should dedicate time to make sure it’s set up correctly and functioning properly.
See also: SecurityMetrics HIPAA Guide
The last component of managing HIPAA compliant firewalls is log management.
Log management also plays a vital role in monitoring firewalls. Set up logging so you have real-time alerts and backtracking to discover what occurred during a problem. Logs keep track of both normal and potentially damaging user actions happening against a firewall and help prevent, detect, and minimize the impact of a data breach. If event log software is configured correctly, administrators can be alerted if firewall logs indicate an attack.
Often, the volume of log data can be overwhelming, but it’s important (and required) to review firewall logs in order to identify patterns and activity that indicate attempts to breach security. There are many great log monitoring solutions available to help organizations handle large volumes of log data and identify events that may require you to take action. Take time to shop options and find a solution that works best for you.
To take advantage of log management, look at your security strategy and make sure these steps are taken care of:
Organizations should review their logs daily to search for errors, anomalies, or suspicious activity that deviate from what’s normal.
Nearly all firewalls have very limited logging space. It’s important to set up a logging server somewhere in the office and configure the firewall logs to go to that server. Software on the logging server can monitor logs from the firewall, as well as from all other systems, and send an email or text alert if it detects you’re under attack.
This is only a short summary of how to install, configure and maintain HIPAA compliant firewalls. Remember, firewalls aren’t just a plug-and-play technology. You have to review them regularly to make sure they’re configured properly. You also need to store and review firewall logs to catch any potential data breaches.
To ensure your firewall does what it’s supposed to, consult with a HIPAA security professional. You’ll want to discuss what firewall types you need to use and which firewalls to purchase. This will prevent common mistakes and ensure everything is set up correctly.
For more information on HIPAA Compliant Firewalls, see our free HIPAA Guide and White Paper, How to Implement and Maintain HIPAA Compliant Firewalls.