Payroll Phishing Emails Attack Hospital and Healthcare Security
Essentially, the hackers steal paychecks from right under their noses.
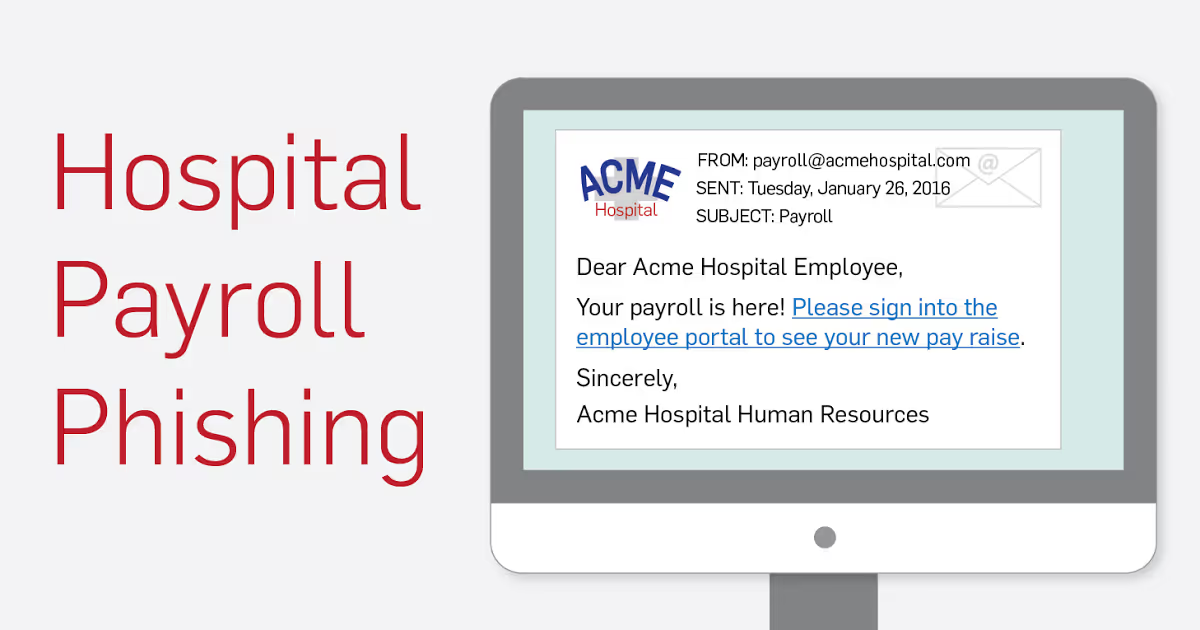
Essentially, the hackers steal paychecks from right under their noses.

We’ve heard a lot about hackers going after patient medical records. It’s a very tempting target for attackers because of the high black market value. A stolen chart might be worth as much as $50 on the black market. One Medicare number can cost as much as $470.
But… there are other options for hackers looking to make a quick buck (or lots of bucks) while attacking healthcare, such as exchanging trade secrets…or stealing paychecks.
In fact, I’ve personally seen an increase in successful phishing attacks targeting information other than medical data in a hospital environment. According to Sophos, 156 million phishing emails are sent every day, and 80,000 people fall for them. Every day.
Using somewhat mundane phishing attack methods, attackers can hijack a hospital’s employee payroll and reroute the money to anonymous bank accounts.
Here’s how it’s done:
Essentially, the hackers steal paychecks from right under their noses.
I know what you’re thinking. “You'd have to be pretty stupid to fall for that!” Well I can tell you more than one neurosurgeon has, and they are pretty smart cookies.
But how would an attacker make it look like an email came from an internal HR department? There are protections in place right?
Well hopefully, but let’s go through the above steps again and add just a little more sophistication as I walk you through this example phishing hack.
All too often hospitals are prime targets of social engineering attacks that can expose what seems like benign data. A single email from HR will often have everything needed, including actual staff names, to craft a believable email. If that doesn't work, borrowing logos and other resources from the hospital website can get the job done.
This is the most difficult part of the attack. An attacker needs email addresses and most websites don’t have many emails listed. But attackers notice email naming conventions, such as: first.last@victimhospital.org. Some hospitals have a list of their top doctors, so if an attacker puts two and two together...
An attacker’s first attempt to send an email with a spoofed from: sam.secretary@victimhospital.org will probably fail because...IT checks for attacks like that. But clever hackers will likely send the email again from sam.secretary@victimhospital.net. The email will probably go through. Of course 20 minutes prior, they registered victimhospital.net with a stolen credit card.
Renowned neurosurgeon Dr. Ima BrainStein gets an email from Sam in HR saying “Hi Dr. Brainstein. You received a raise. Please login to the employee portal to confirm.” Dr. Ima clicks on the employee_portal.victimhospital.org link which redirects to the spoofed employee_portal.victimhospital.net page which is remarkably similar to the real login page.
After logging in, Dr. Ima Brainstein is disappointed by the message. “Sorry, the employee portal is down for maintenance. Please try again in a few minutes.”
The attacker is not not disappointed, as he just captured Dr. Ima’s credentials:
username: “brainstein.ima”
password: “I_got_my_D3gree_online!”
See also: SecurityMetrics HIPAA Guide
Phishing attacks are a very serious crime and happen more frequently because they are relatively easy to pull off.
None of the steps above took stellar hacking skills, just a basic understanding of how email and domain names work.
See Also: Fighting Phishing Email Scams: What You Should Know
Of course there are much more complicated attacks that involve exploiting obscure vulnerabilities in web servers, email servers, and various web protocols. But unfortunately many hospitals are riddled with simple vulnerabilities.
A vulnerability is a flaw in components, procedures, design, implementation, or internal controls. Countless vulnerabilities exist in the healthcare industry today, such as weak passwords, unpatched software, negligent employees, coding problems, and misconfigured firewalls. Not to mention massive amounts of sensitive data walking in and out the front door into the wild west of employee's home computers, personal laptops, and mobile devices.
Here are a few of the most likely vulnerabilities that could allow a payroll phishing or other attack to occur.
Healthcare employees are the largest unavoidable threat to healthcare data security. Many can be socially engineered, use weak passwords, and surf the web unrestricted at work. They walk out the door every day with a million bucks worth of HIPAA fines on a personal laptop protected with the password: password.
Healthcare IT staff goes to great lengths to make remote access a smooth experience for the many telecommuters that work in the industry. They set up bulletproof VPN's and two factor authentication and create the perfect firewall rule set. Then while using public Wi-Fi on a beach in Maui, a hacker breaks into the laptop. The hacker is now a user on the internal network.
Healthcare environments, especially hospitals, have a difficult time controlling their location’s physical security, and the physical security of protected health information (PHI).
Here are some examples of physical security problems I see when I walk into hospitals:
See also: PHI is Literally Everywhere
Most hospitals have a great internal IT staff who know what they are doing, security-wise. But, they’re overwhelmed due to inherent maintenance/control/enforcement nightmares inside hospital politics. A top producing business associate, such as a pharmacy, may have its own ideas and different rules for its own network. To keep high-producers happy, security policies have a habit of developing short-sighted, though financially expedient, exceptions. The cycle is not favorable for hospital and healthcare security.
The good thing is, all of these vulnerabilities can be managed. Here are some great ways to avoid attacks like the payroll phishing attack at your healthcare practice.
Payroll phishing is a relatively easy way for hackers to rake in the dough. It does take some luck, but I predict we will see more attacks like this as more attackers realize the inherent value not just in healthcare data, but exploiting the employee data of all those who work in the healthcare industry. When strategizing and planning for HIPAA compliance, remember that enforcing the policies procedures surrounding hospital and healthcare security are crucial to protecting patient and employee data.