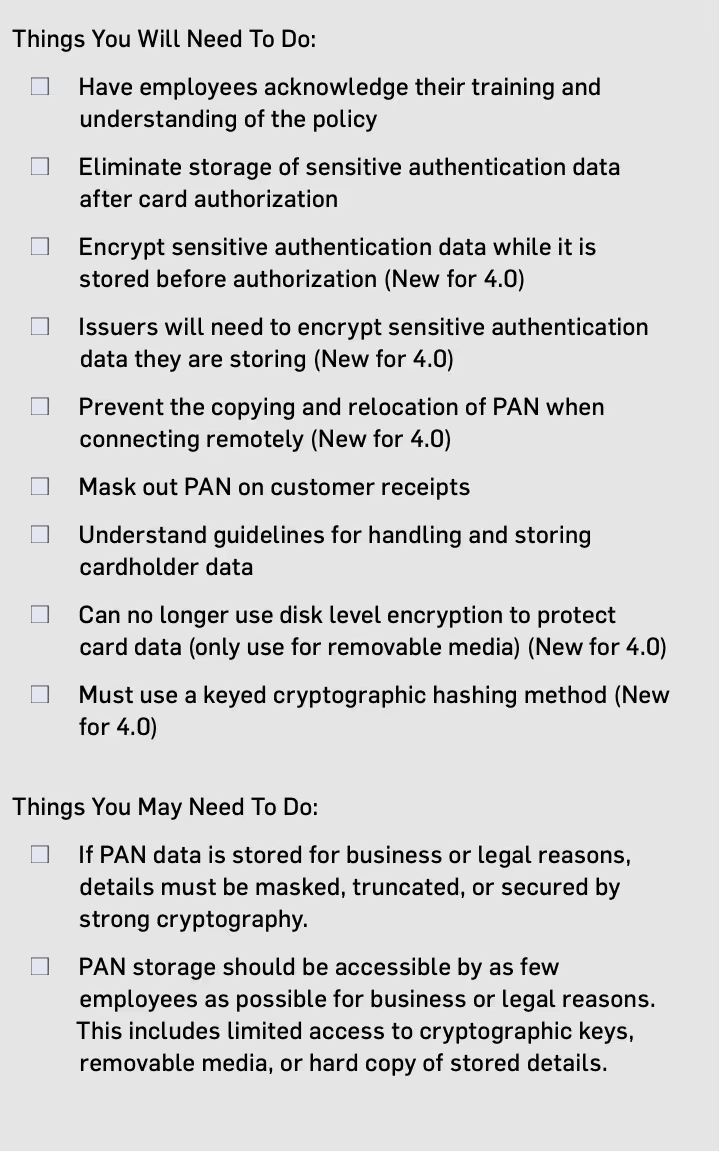
PCI DSS Requirement 3: What You Need to be Compliant
PCI DSS Requirement 3 involves protecting card data storage.

PCI DSS Requirement 3 involves protecting card data storage.

Are you compliant with PCI DSS Requirement 3? This requirement involves protecting card data storage.
When cybercriminals hack a payment system, they can’t steal cardholder data that isn’t there. That’s why it’s important to keep your system clean of insecurely stored card data. The problem is that unencrypted payment card data has a way of creeping in where you least expect it.
Not protecting the encryption key location using a solid PCI DSS encryption key management process is like storing your house key in your front door lock.
Stored card data must be encrypted using industry-accepted algorithms (e.g., AES-256). Unfortunately, many merchants don’t know they are storing unencrypted Primary Account Numbers (PANs).
In the latest study by SecurityMetrics, 84% of merchants were found to store unencrypted PANs.
Some places that may be hiding card data unintentionally include:
See also: SecurityMetrics PCI Guide
Not only must card data be protected to comply with PCI requirement 3, but also the encryption keys must be protected. Leaving encryption keys unprotected is like storing your house key by leaving it in your front door lock, so it’s critical to use a solid PCI DSS encryption key management process.
“Remember, payment card data can easily leak due to poor processes or misconfigured software. Start by looking where you think the data is, and then look where it shouldn’t be” (2025 PCI Guide).
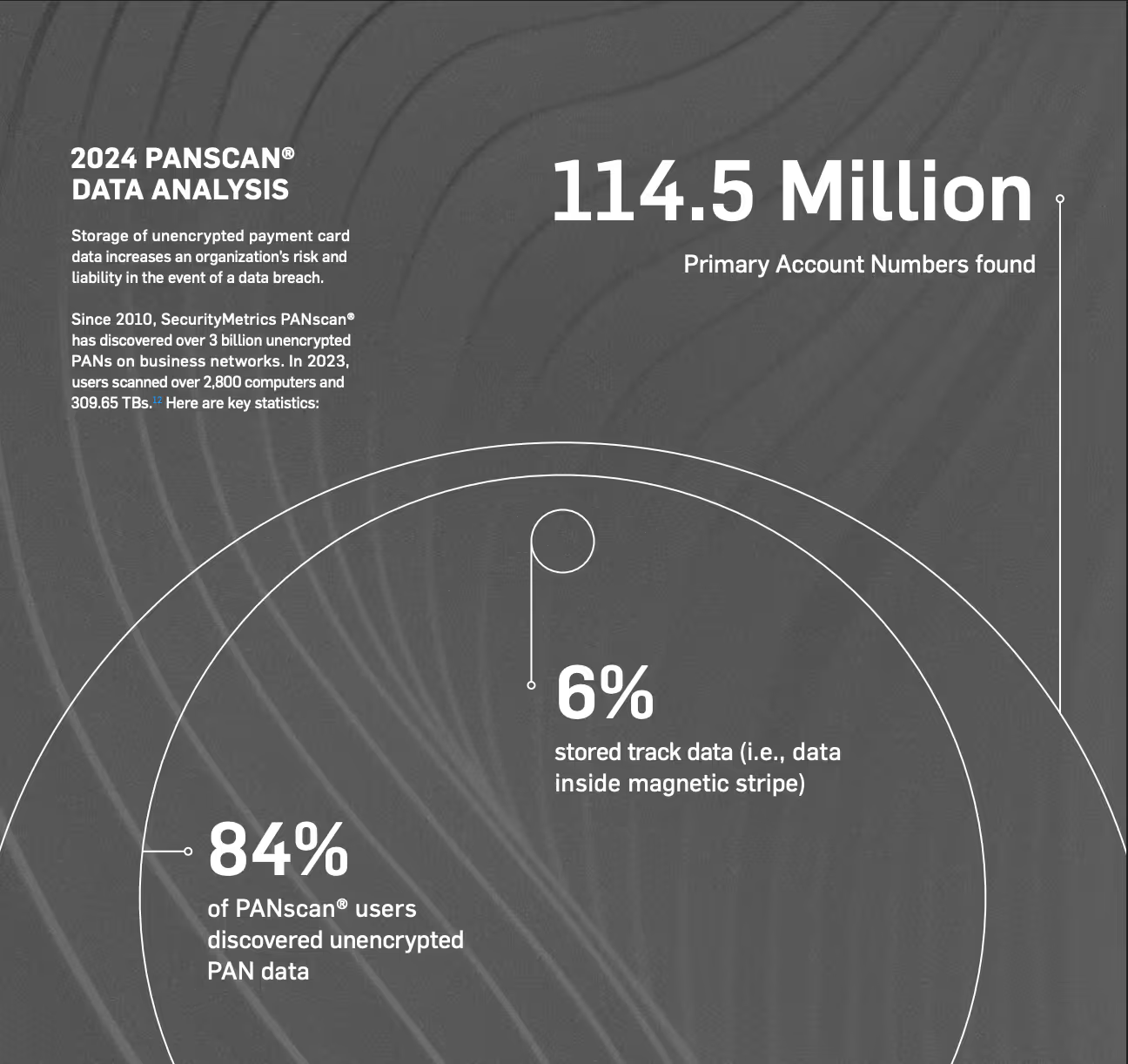
Payment card data can easily leak due to poor processes or misconfigured software. You must look where you think the data is, and then look where it shouldn’t be.
PCI DSS requires a current diagram for all card data flows in your organization. A card data flow diagram is a graphical representation of how card data moves through an organization. As you define your environment, ask all organizations and departments if they receive cardholder information, and determine how their answers may change your current understanding of your organization’s card data flows.
“Create data flow diagrams for your entire organization (on all information you deem sensitive), not just for your CDE environments. You might miss something if you only focus on the CDE and CHD” (Ben Christensen, SecurityMetrics Senior Security Analyst).
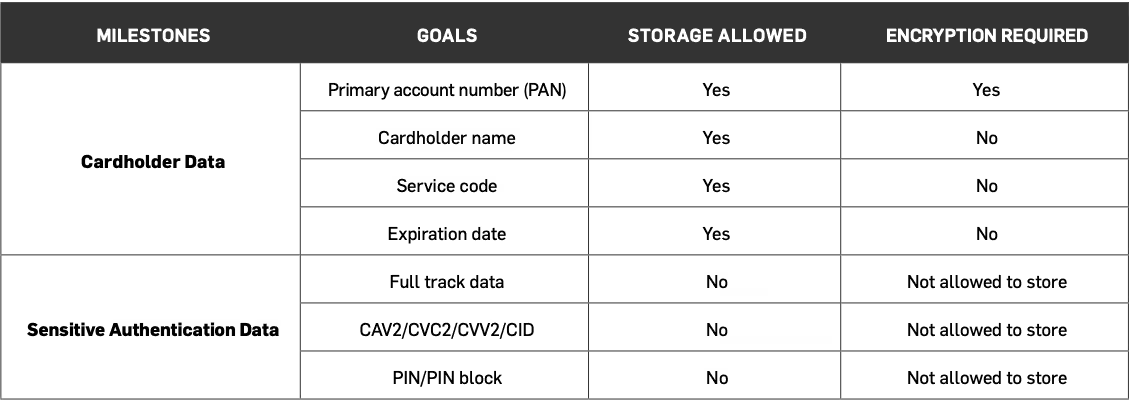
In addition to looking at data flows and processes, you should regularly run a cardholder data discovery tool (such as PANscan® or PIIscan) on your systems. These tools help identify the location of unencrypted PAN. Knowing where PAN data is stored helps confirm if your CDE is secure. It also helps identify which processes or data flows might need to be adjusted.
Assign the responsibility of keeping unencrypted card data off your systems to an individual or team. Have them define and follow a process of periodic data discovery cycles to recheck and ensure systems remain clean of unencrypted card information.
See also: How Much Credit Card Data do You Store? (It’s More Than You Think.)
Here are a few more things to think about while fulfilling Requirement 3: