
An in-depth look at the PCI Security Standard Council’s recent MFA guidance supplement and what it means for your organization.

Merchants use the 2018 SecurityMetrics PCI Guide both as a desk-side PCI reference and as a tool to direct and track their organizations’ internal PCI compliance efforts. But, there’s also another side to the Guide.
At SecurityMetrics, our mission remains to help you close data security and compliance gaps to avoid data breaches.
As plans to reopen economies move forward around the world, the entire cybersecurity industry–including the SecurityMetrics Security Operations Center (SOC)–is being challenged in new and unexpected ways.

Whether you’re a small business owner or the CISO at a large enterprise, finding good cybersecurity conferences is a necessary task to continue security education and explore the latest technology and innovative solutions.

The SecurityMetrics PCI DSS Compliance Guide Wins “Most Innovative Cybersecurity Book” Award.

We picked the top 10 most common flaws in SMB networks we see when setting up and managing firewalls for our customers.

As part of our objective to help companies secure peace of mind, we have selected our top blogs for 2021 to help you maintain and strengthen your security.

Current COVID-19 Cyber Threats The UN Agency WHO has reported a 500% increase in cyber security incidents over the same period last year.
The PCI Guide includes interactive and printable IT checklists for every requirement, stories and tips from our security analysts (QSAs), forensic data breach research data, as well as the latest updates on PCI DSS compliance.
The SecurityMetrics Podcast is a weekly podcast with regular host and Principal Security Analyst Jen Stone (MCIS, CISSP, CISA, QSA), along with a variety of experts in the data security and compliance space.

We create and publish our HIPAA Guide each year: to give healthcare IT and HIPAA leaders an up-to-date resource to direct and focus their HIPAA compliance efforts to the areas that are quick and impactful.

While performing an external network layer penetration test I encountered a host that presented a single page that was essentially blank...

These top SecurityMetrics blog posts help you understand and implement some of the most foundational data protection principles. Our goal it to help you close gaps in security and avoid a data breach in 2019.
The importance of cybersecurity: SecurityMetrics Academy is a free educational course designed for anyone who wants to learn about data security.
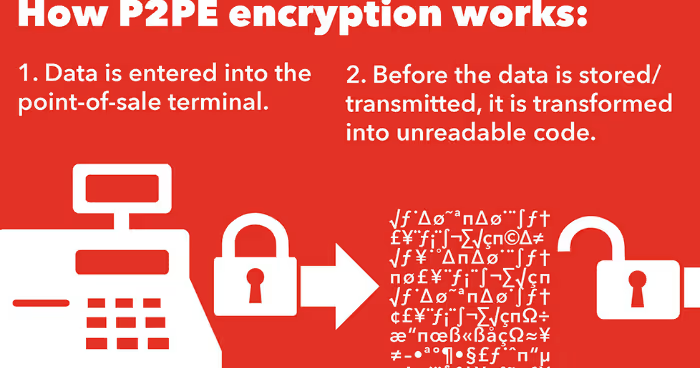
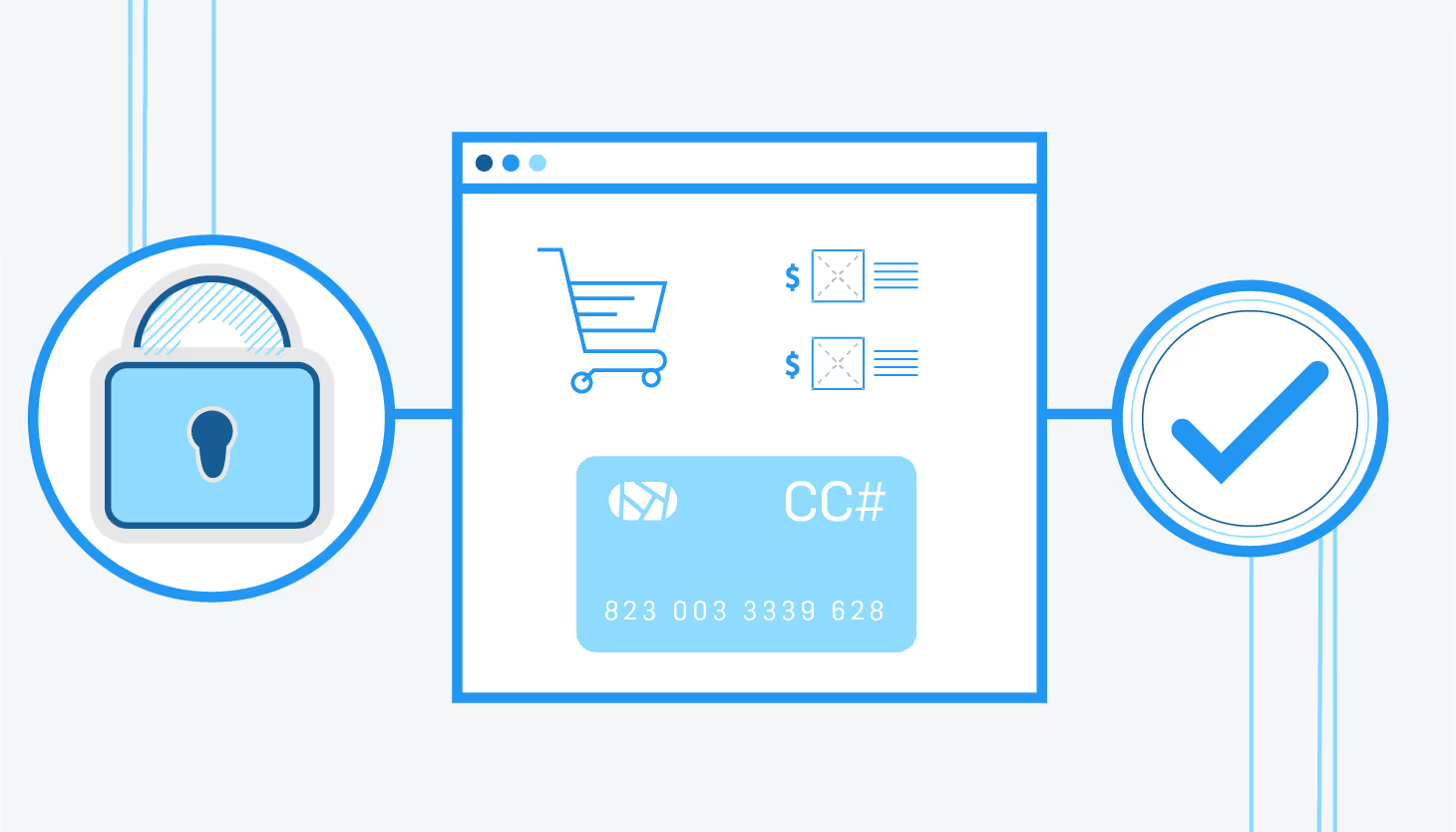
There’s only one way to avoid leaving ten-second holes in security. Encrypt card data at the exact millisecond of collection.

Covered entities don’t have the option to hide behind BAA if a Health and Human Services (HHS) auditor comes knocking.

Businesses around the world call us in a panic, needing to decipher what went wrong with their security.

Learn what to do when you are hacked (or suspect you’ve been hacked).
Understand HIPAA Privacy and Security Rules, and how they apply to your organization.
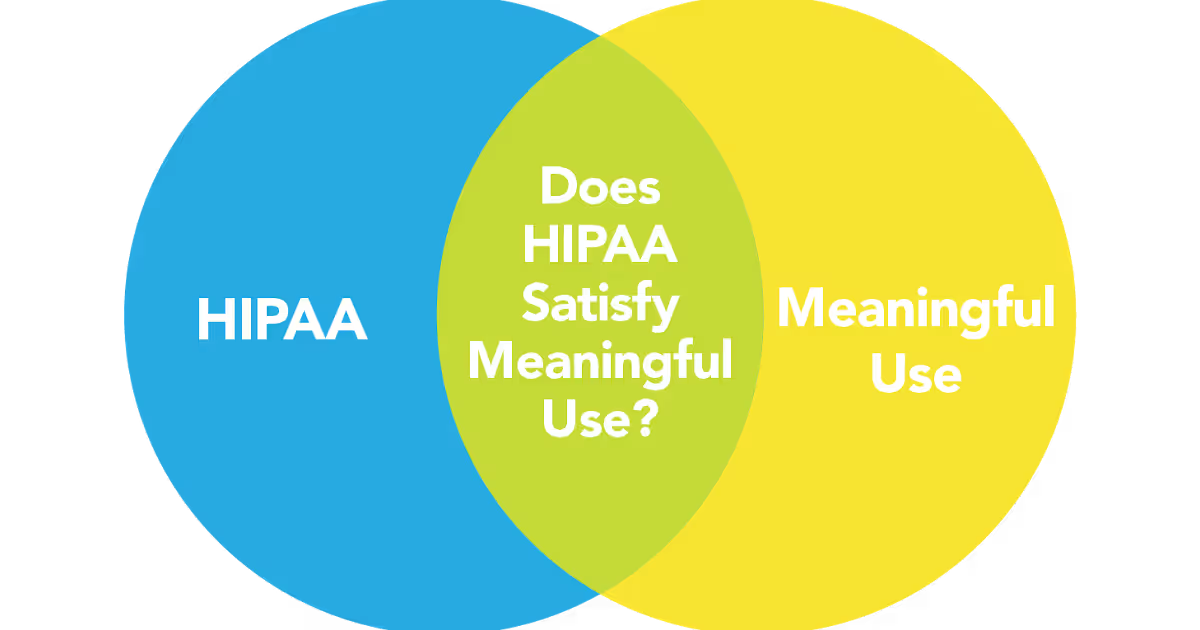
Many healthcare professionals don’t completely understand how the specific requirements of HIPAA and Meaningful Use relate.

The first step in preparing for a HIPAA audit is to create a detailed compliance plan.

All stages of Meaningful Use include some element of a risk analysis and data security.