Like a security guard, firewalls control what goes in and what comes out.

With over 20 years in the industry, we have found that these HIPAA compliance best practices are most helpful in securing your organization.

A directory traversal, CVE-2019-10717, was identified on BlogEngine.NET applications versions 3.3.7 and earlier through the /api/filemanager endpoint.

Attackers: Known or Unknown? That is the question.

This post will highlight changes made to the SAQ C-VT version 4.0 and provide guidance on how to comply with newly added requirements.

Rather than worrying about the new PCI requirements, you can prepare for PCI DSS 4.0 by focusing on your current PCI DSS compliance efforts and choosing to think of 4.0 as a timely addition that will provide more defenses against developing attack methods.

Contrary to popular belief, addressable does NOT mean optional.
The #1 most important piece of a data loss prevention method? An intrusion detection system.
Small businesses often find themselves caught between limited resources and the threat of cybersecurity breaches. To avoid a data breach, here are 7 common Mistakes in small businesses security.

To effectively protect your business, it's crucial to understand the various types of phishing tactics and how to prevent them.
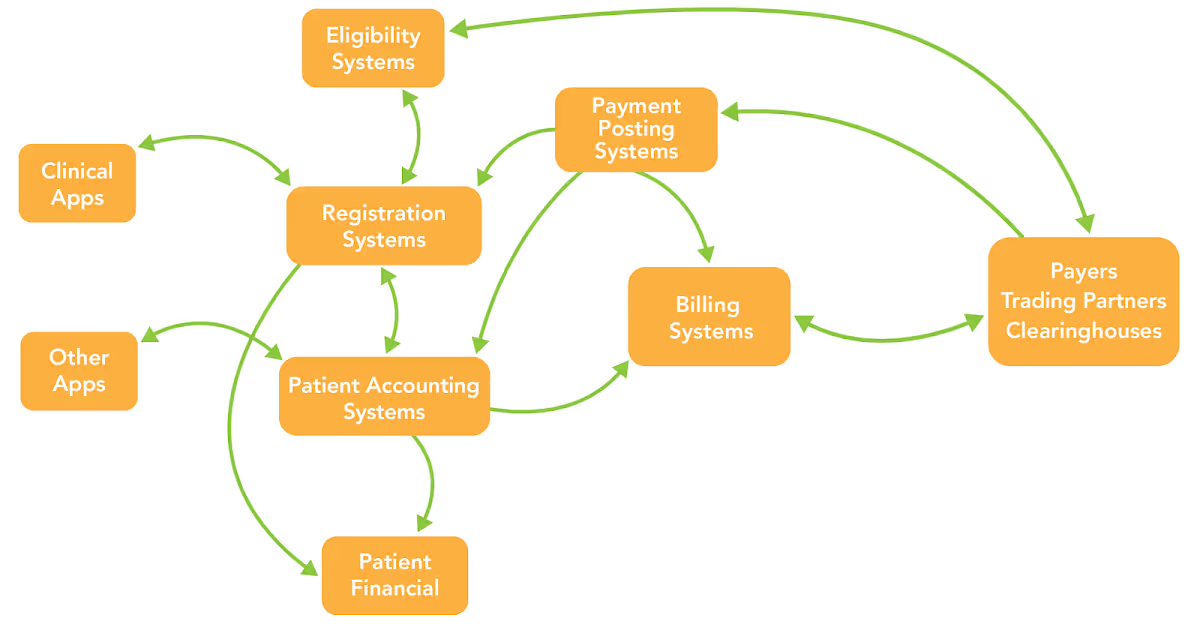
How can you secure your organization without knowing how patient data travels?

Learn why restricting employee access to data helps protect your business.

See why you should comply with PCI DSS Requirement 7 and restrict employee access to sensitive data.

Depending on a few factors, cyber insurance premiums can cost from $650 to easily over $120,000 annually.

When those defaults aren’t changed, you give hackers Wonka’s Golden Ticket into your system.

If you don’t have a compelling business need to store PAN, don’t store it!

Fight against social engineering by providing proper regular staff training.

A HIPAA document is more than a policy: it's proof you care about protecting patient data.

Biometrics more accurately associates a specific individual to a device or system.

On January 1, 2017, SHA-1 was officially no longer accepted by web browsers.
Find out some of the essentials to include in your incident response plan.