
Healthcare security gaps often stem from communication issues. It’s common to see executives and practice leads who aren’t listening to their staff about their current state of compliance and security.

A penetration test will give you a holistic view of what your security system truly looks like. Organizations with poor security practices across their environment leave themselves vulnerable.

The minimum necessary requirement is a key part of the HIPAA Privacy Rule. The goal of this requirement isn’t to encourage organizations to perform the minimum necessary, but rather for organizations to only use and disclose the minimum amount of PHI necessary

Regular vulnerability scans are a critical preventative security control as they detect and assess known weaknesses that may be opening up your systems, applications and networks to undue risk of intrusion. Vulnerability scanning is not penetration testing.

You need a team to choose and manage an IDS/IPS. Whether it’s the responsibility of your IT Security Team,Data Loss Prevention Team, a managed service provider, or a designated co-managed team consisting of security-related department heads.

More recently, password length, in the form of longer, memorable word strings have proven to be a more important security practice than the use of shorter complex passwords.

You should implement encryption to protect PHI any time it is stored.

Monitoring audit logs for all critical systems and devices in your environment is key to understanding what types of events and actions occur on a daily basis, allowing you to establish a baseline of what is considered normal system activity.

Remote access to tools and data is essential to employees who work from home or are unable to go into the office for health or other logistical reasons.

Whenever a system is configured make sure you know exactly what is running and also what is necessary to allow the system to perform its intended function.

While every organization is different, the end goal of practicing good cyber hygiene is to identify vulnerabilities, minimize risk exposure, and reduce the potential for a breach.

Fully understanding all the PHI you have, where it is stored, what processes touch it, and how it is used in your organization is critical to enabling a business to properly handle and secure PHI.

Yet a complete and thorough risk analysis is one of the best ways for you and your organization to make intelligent and informed business decisions

The SAQ A-EP PCI assessment is for merchants who have an e-commerce card data flow that is not entirely outsourced to a PCI validated third-party service provider.

HIPAA laws and cybersecurity are not simple. The 2023 HIPAA Guide breaks down HIPAA guidelines into actionable steps and easy-to-understand information so that your healthcare staff can be fully educated on data privacy and protection.

We created our Guide to HIPAA compliance to help you close gaps in security and compliance, ultimately helping you avoid a data breach.

One of the easiest ways to make cybersecurity training more interesting is by making it fun. Here are five tips for making workforce security training fun and memorable.

PCI DSS 3.2 has added and removed new requirements to the SAQs.
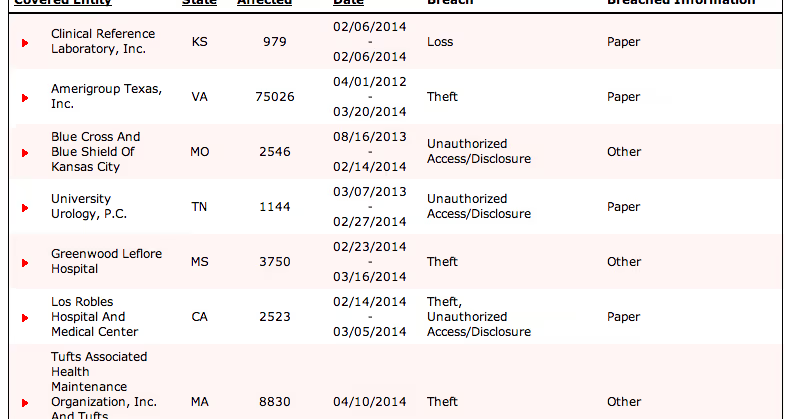
Brand degradation and patient exodus will likely occur every time an organization shames their name through a data breach.

Hackers bike around the city with their laptops in a discreet backpack (or strapped in a bike trailer) and search for unprotected wireless networks.

Unencrypted payment card data is relatively simple for a hacker to detect, scoop up, and steal.

Given the stated importance and heavy consequences associated with the risk analysis, you may want to consider working with a HIPAA security expert.